Private keys play a critical role in securing digital transactions and personal data. As unique sequences of characters, they function within encryption frameworks to authenticate and control access to information. Understanding private keys involves recognizing their relationship with public keys, securing your assets, and implementing robust storage strategies. The risks associated with losing a private key can lead to irreversible consequences. What steps can you take to guarantee your private keys remain secure and effective?
Key Takeaways
- Private keys are essential for asymmetric encryption, enabling secure communication and digital identity management.
- Keeping private keys confidential protects sensitive information and ensures only authorized users can access digital assets.
- Loss of a private key results in irreversible access loss, making it impossible to retrieve associated funds or records.
- Using strong passwords and two-factor authentication enhances private key security against unauthorized access.
- Best practices include hardware wallets and secure backups to safeguard keys from digital threats and risks.
Understanding Cryptographic Keys
Cryptographic keys serve as the backbone of secure digital communication, as they enable the encryption and decryption processes that protect sensitive information. Understanding cryptographic keys entails recognizing their role in various security protocols, as well as the essential aspects of key management.
Key points to contemplate include:
- Types of Keys: Symmetric and asymmetric, each serving different use cases.
- Key Length: Longer keys enhance security but may impact performance.
- Key Rotation: Regularly updating keys helps mitigate risks associated with theft.
- Access Control: Limiting who can access keys is fundamental to maintaining security.
Effective key management fosters a robust framework, ensuring that cryptographic keys are generated, stored, and destroyed safely, thereby maintaining the integrity of your digital communications.
What Are Private Keys?
Private keys, which are essential components of asymmetric encryption, provide a means for individuals and organizations to securely manage their digital identities and communications. A private key is a cryptographic key that must be kept confidential, while its counterpart, the public key, can be shared openly.
There are various private key types, including:
- RSA: Uses large integers for secure data transmission.
- ECDSA: Employs elliptic curve mathematics for efficient security.
Private key generation typically involves random number generation processes, ensuring that the keys are unpredictable and unique. By understanding these concepts, you’ll appreciate the critical role private keys play in preserving the integrity and confidentiality of digital transactions, making them indispensable for anyone engaged in online activities.
How Private Keys Work
Understanding how private keys work is essential for grasping the underlying mechanics of secure digital communications. Private keys are a vital element in secure data transmission, providing key authentication and ensuring that only the rightful owner can decrypt messages. Here are three important aspects of how private keys operate:
- Key Generation: During this process, a cryptographic algorithm creates a unique private key, often paired with a public key.
- Encryption: When you send a message, it encrypts using your recipient’s public key, but only their private key can decrypt it.
- Digital Signatures: You can sign transactions with your private key, verifying your identity and the integrity of the information transmitted.
In essence, private keys form the backbone of secure and trusted digital exchanges.
The Importance of Keeping Your Private Keys Safe
The security of digital transactions largely hinges on your ability to keep your private keys safe, as they are the gatekeepers to your sensitive information and assets. The private key importance cannot be overstated; if someone gains access to your keys, they can control your digital wealth.
To guarantee key security, you should employ various key security techniques, including:
- Strong Passwords: Utilize complex, unique passwords to protect access points.
- Two-Factor Authentication: Implement additional authentication layers for enhanced security.
- Cold Storage: Keep private keys offline to minimize exposure to online threats.
- Hardware Wallets: Use dedicated devices designed for secure key management.
Common Ways to Store Private Keys
When considering how to store your keys securely, you have several common methods, each with its unique advantages and disadvantages. Choosing the right storage solution can enhance your security posture and minimize risks. Here are three popular options:
- Cold Storage: This method involves keeping your private keys completely offline, often using paper wallets or USB drives, which reduces vulnerability to online threats.
- Hardware Wallets: These specialized devices securely store your private keys and are designed to safeguard against hacking, even when connected to the internet.
- Software Wallets: While more convenient for regular transactions, these wallets are stored on your device, leaving them susceptible to malware and phishing attacks.
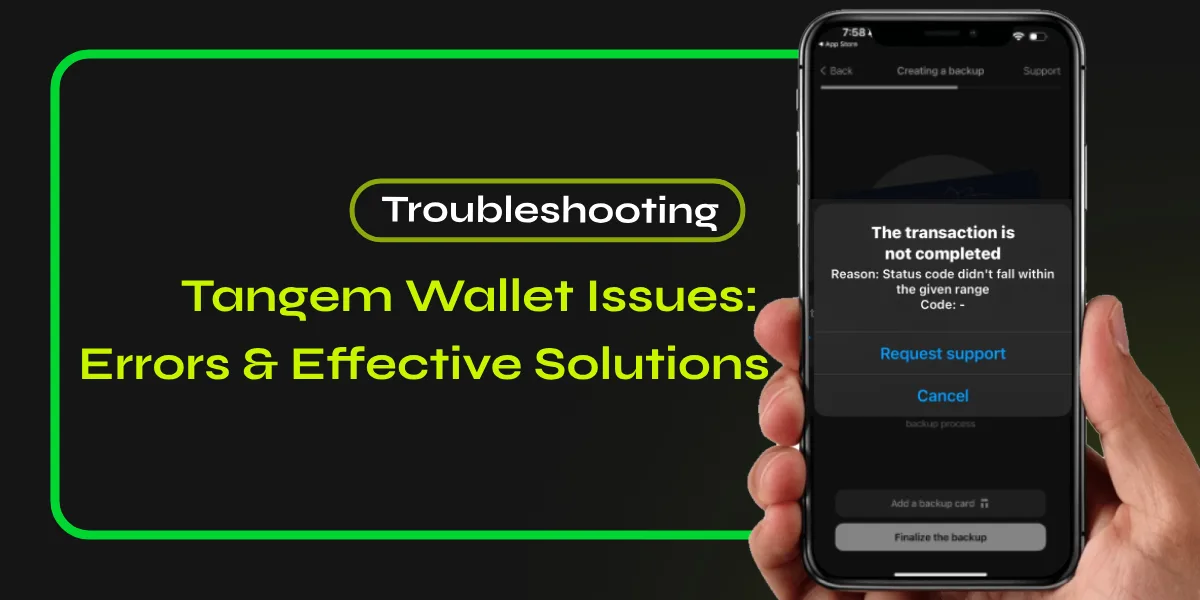
The Risks of Losing Your Private Key
Losing your private key can lead to irreversible consequences, including the permanent loss of access to your cryptocurrency assets. Without the private key, you’re unable to release your digital wallet, making any coins or tokens within it irretrievable. This situation highlights the significance of private key recovery methods, which can often be complex and sometimes impossible.
Lost key consequences include:
- Complete loss of funds: No way to recover the cryptocurrencies stored.
- Financial impact: The investment becomes worthless without access.
- Loss of transaction history: You lose all records associated with your wallet.
To avoid these dire outcomes, it’s essential to implement secure storage solutions for your private keys and regularly back them up.
Differences Between Private and Public Keys
To understand the differences between private and public keys, it’s essential to grasp their definitions first. Private keys are your exclusive tools for signing transactions and decrypting messages, while public keys work as your digital address for receiving encrypted information and verifying signatures. This distinction not only highlights their roles in encryption and decryption but also outlines important aspects of ownership and control within cryptographic systems.
Key Definitions Explained
Understanding the distinction between private and public keys is essential in the domain of cryptography, as these two components work together to secure communications and safeguard sensitive information.
- Private Key: A secret component known only to the key owner, used for signing and decrypting data during key generation.
- Public Key: A widely distributed counterpart, enabling others to encrypt messages or verify signatures without revealing the private key.
- Key Management: Encompasses the strategies and techniques used to create, distribute, store, and manage these keys, ensuring their protection and minimizing unauthorized access.
These differences are fundamental for maintaining security in digital interactions, as they help determine how you handle key generation and overall data protection strategies.
Encryption and Decryption Roles
In the domain of cryptography, private and public keys each play pivotal roles in the processes of encryption and decryption, functioning as the cornerstones of secure communication. Public keys allow users to encrypt data, guaranteeing that only the holder of the corresponding private key can decrypt and access the original message. This asymmetric system boosts data integrity, as only authorized users can access sensitive information.
Key characteristics include:
- Public Keys: Shared openly, enabling anyone to encrypt messages for a specific recipient.
- Private Keys: Kept secure, providing the only means to decrypt messages encrypted with the corresponding public key.
This dual approach not only guarantees data integrity but also enhances algorithm efficiency, allowing for rapid processing without compromising security.
Ownership and Control Differences
Ownership and control play essential roles in distinguishing private keys from public keys. Understanding these differences can help clarify the ownership implications and control dynamics in cryptographic systems.
- Private Key Ownership: You solely own the private key, granting you complete control over the associated assets, ensuring that only you can access or authorize transactions.
- Public Key Accessibility: Public keys are non-secret and available to anyone, allowing them to encrypt information intended for you, without risking ownership.
- Trust Relationships: Ownership of a private key establishes trust; without it, you cannot prove ownership or control over the digital assets secured under it.
Understanding these differences is vital for maneuvering the complexities of digital security.
Best Practices for Private Key Security
To effectively safeguard your private keys, it’s crucial to implement robust security practices that can reduce the risk of unauthorized access and loss. Utilizing hardware wallets is one of the most effective methods, as they store your keys offline, making them less vulnerable to hacking attempts. Additionally, you should create secure backups stored in various locations, guaranteeing you can recover your keys if necessary.
Key practices include:
- Use strong passwords: Combine upper and lowercase letters, numbers, and symbols.
- Enable two-factor authentication: This adds an extra layer of security.
- Regularly update your software: Confirm that your wallet and security tools are current to defend against vulnerabilities.
Following these practices can greatly enhance the security of your private keys.
Frequently Asked Questions
Can I Generate My Own Private Key?
Yes, you can generate your own private key. Just make certain you’re using a reliable method for private key generation and prioritize secure storage afterward to protect your assets against unauthorized access and potential loss.
What Happens if Someone Else Gets My Private Key?
If someone else gets your private key, they can access your assets, steal your funds, and compromise your key security. Protect against key theft by using secure storage methods and keeping your key confidential.
Are Private Keys Unique for Each User?
Yes, private keys are unique for each user. This uniqueness is essential, as it guarantees your control over your assets and prevents unauthorized access. Understanding these private key characteristics can help you safeguard your digital possessions effectively.
Can I Use a Private Key for Multiple Accounts?
Using the same private key across multiple accounts is like leaving your front door wide open. It weakens your account security and invites trouble. Each account deserves its unique private key to stay safe from prying eyes.
How Do I Know if My Private Key Is Compromised?
To know if your private key’s compromised, regularly monitor your accounts for unauthorized access and follow key management practices. If you suspect a breach, immediately change your keys to guarantee your private key security remains intact.
Conclusion
In conclusion, private keys play a pivotal role in preserving the privacy and protection of your digital assets. By safeguarding these essential codes, you not only secure your sensitive information but also maintain the integrity of your online transactions. Prioritizing the protection of your private keys guarantees your financial freedom and fosters trust in digital environments. Stay vigilant, utilize secure storage solutions, and implement best practices to prevent potential pitfalls in your personal cybersecurity strategy.