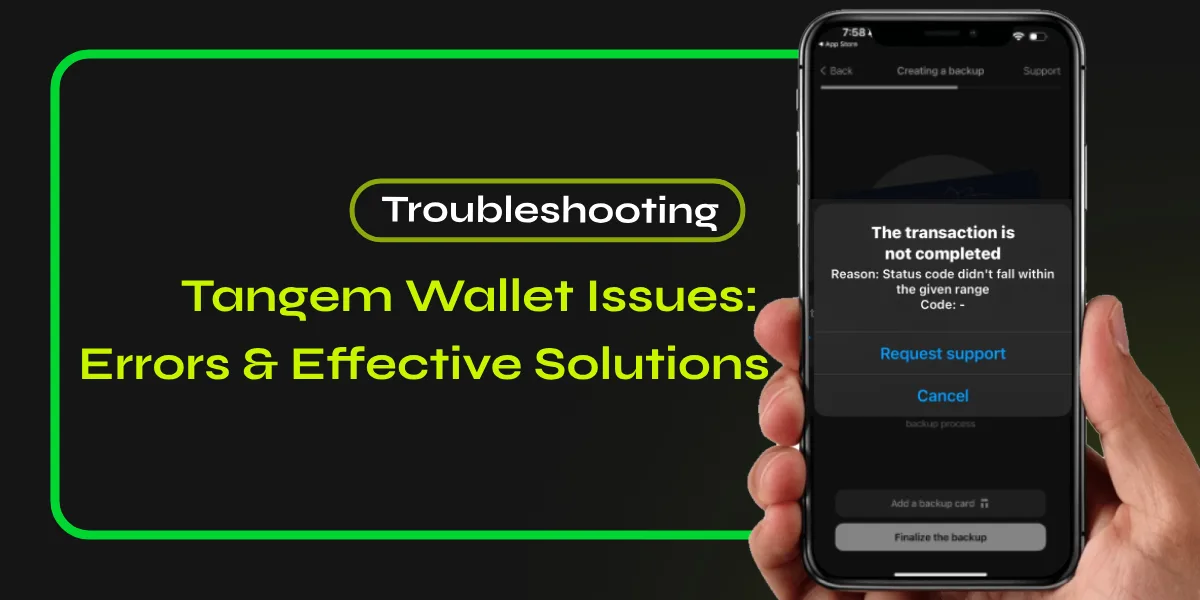
Recovering a hacked crypto wallet requires a methodical approach, particularly for beginners unfamiliar with the complexities involved. Key steps include isolating the device from the internet, reviewing transaction histories for unauthorized activity, and informing any associated exchanges. Additionally, implementing two-factor authentication (2FA) and leveraging backup phrases are critical for regaining access. Effective documentation of the incident enhances recovery efforts, but understanding these elements is essential in traversing the aftermath of a wallet compromise. Next, one must explore the implications of these actions.
Key Takeaways
- Isolate your compromised device from the internet to prevent further unauthorized access immediately after detecting a hack.
- Report suspicious activities to your wallet provider and any relevant exchanges to initiate recovery support.
- Utilize your wallet’s recovery phrase or backup options to restore access to your wallet securely.
- Strengthen security measures, including enabling two-factor authentication and using strong, unique passwords for all accounts.
- Regularly monitor account activity to catch any unauthorized transactions early and adjust security protocols as needed.
Understanding the Basics of Crypto Wallets
Cryptocurrency wallets, which serve as important tools for managing digital assets, can be categorized into several types, each with distinct functionalities and security features that users should understand. The primary classifications are hot wallets and cold storage wallets.
- Hot Wallets:
- Connected to the internet, facilitating real-time transactions.
- Offers convenience but may pose hot wallet security risks due to potential hacking.
- Cold Storage:
- Offline storage options, like hardware and paper wallets, providing enhanced security.
- Ideal for securing large volumes of cryptocurrency, as they are impervious to online threats.
Understanding these distinctions is vital for users aiming to protect their assets while engaging in cryptocurrency transactions. Choosing the right wallet type greatly impacts both accessibility and security.
Recognizing Signs of a Hacked Wallet
Recognizing the signs of a hacked crypto wallet is essential for maintaining security and protecting digital assets. Key indicators include unexplained transactions appearing in account statements, an inability to access the wallet despite using correct credentials, and unexpected changes to account settings or balance information. Familiarizing oneself with these warning signs can help users respond promptly and effectively to potential security breaches.
Unexplained Transactions Occurring
When a user observes transactions in their crypto wallet that they do not recognize or authorize, it may be a stark indication of a compromised wallet. These unexplained withdrawals, often accompanied by other suspicious activity, can notably jeopardize the user’s crypto assets. Identifying the signs early on is essential to mitigating potential losses.
| Type of Activity | Description |
|---|---|
| Unexplained Withdrawals | Funds withdrawn without user consent |
| Suspicious Activity | Unauthorized changes or unusual logins |
Such transactions should prompt an immediate investigation into the wallet’s security. Users are advised to enable two-factor authentication and regularly monitor their transaction history to safeguard their digital assets effectively.
Inaccessible Wallet Access
As users engage with their crypto wallets, they may encounter challenges that signal potential unauthorized access, often leading to an inability to access their funds. An inaccessible wallet prompts immediate attention, as it can indicate a security breach. Users should be vigilant for signs such as:
- Login failures despite entering correct credentials,
- Unrecognized devices connected to the wallet,
- Notifications of failed attempts to access the account.
In such circumstances, priority should be given to access recovery procedures, which can include verifying security questions, utilizing two-factor authentication methods, or restoring from a secure backup. Promptly addressing these indicators of compromised access can help mitigate further risks and preserve the integrity of one’s crypto assets.
Unexpected Account Changes
Unexpected alterations within a crypto wallet can serve as significant indicators of potential compromise, warranting immediate scrutiny by the account holder. Recognizing these suspicious activities is vital for early intervention and account recovery. Key signs to monitor include:
- Unauthorized transactions: Any transfers or trades initiated without the account holder’s consent should raise red flags, indicating possible hacking.
- Changes in account settings: Alterations to security features, such as password resets or two-factor authentication modifications, may suggest unauthorized access.
- Unfamiliar device logins: Notifications of new device activity highlight potential breaches, requiring further investigation.
Timely recognition of these indicators enables account holders to act swiftly, safeguarding their digital assets while maneuvering through the complexities of crypto security.
Immediate Actions to Take After a Hack
Following the breach of a crypto wallet, individuals must act swiftly and strategically to mitigate potential damages and secure their remaining assets. Initial steps should involve isolating the affected device, disconnecting from the internet to prevent further access, and informing necessary exchanges about potential suspicious activity. Implementing stronger security protocols, such as two-factor authentication (2FA), can enhance future protection. Exploring recovery options may involve restoring wallets from backups or using recovery phrases, if available.
| Action | Details |
|---|---|
| Isolate Device | Disconnect from the internet |
| Inform Exchanges | Report any unauthorized transactions |
| Strengthen Security Protocols | Enable two-factor authentication (2FA) |
Securing Your Other Digital Assets
Securing other digital assets is an important step following a crypto wallet hack, as vulnerabilities may extend beyond the compromised account. Implementing strong, unique passwords for each account is essential; these passwords should ideally include a combination of upper and lower case letters, numbers, and symbols to enhance their complexity. Additionally, enabling two-factor authentication (2FA) adds an extra layer of security, requiring not just a password but also a secondary verification method, which can considerably reduce the risk of unauthorized access.
Use Strong Passwords
A robust password strategy greatly enhances the security of digital assets, including cryptocurrency wallets, online banking accounts, and email services. To effectively create passwords, users should prioritize complexity by including upper and lower case letters, numbers, and special characters. Password managers can considerably facilitate this process, as they allow users to generate, store, and autofill passwords securely.
| Feature | Description | Benefits |
|---|---|---|
| Password Complexity | Minimum of 12 characters, varied types | Increased resistance to attacks |
| Unique Passwords | Different for each account | Limits damage from breaches |
| Password Manager Use | Secure storage and generation | Simplifies security management |
Enable Two-Factor Authentication
Authentication is a crucial element in the defense against unauthorized access to digital assets, especially in the domain of cryptocurrency wallets and other online accounts. Enabling two-factor authentication (2FA) is one of the most effective authentication methods available.
The two-factor benefits include:
- Enhanced Security: Users must provide a second form of verification in addition to their password, markedly reducing the risk of unauthorized access.
- Versatile Options: Various authentication methods are available, including SMS codes, authentication apps (like Google Authenticator), or biometric recognition, allowing users to choose what best suits them.
- Account Integrity: Implementing 2FA guarantees that even if a password is compromised, the account remains protected through an additional layer of security, making it considerably harder for hackers to gain access.
Contacting Support and Reporting the Hack
Recovering from a hacked crypto wallet necessitates prompt and effective communication with support services provided by the wallet provider or exchange. Users should take precise actions to guarantee their case is managed efficiently, which includes documenting events and notifying authorities. Clear communication aids teams in identifying and mitigating risks associated with the breach. Essential steps include:
- Gathering transaction details and timestamps
- Documenting all suspicious activities observed
- Notifying local authorities or cybercrime units
- Maintaining records of correspondence with support
Steps to Restore Access to Your Wallet
Following a hack, restoring access to a crypto wallet involves several essential steps that users must undertake methodically to safeguard their assets and regain control. The first step in wallet recovery techniques is to verify the integrity of the backup phrase, which serves as the foundational element for accessing the wallet. Users should confirm that their backup phrase is stored securely, ideally in a physical format away from internet access, preventing further compromises.
Next, they should utilize the wallet’s recovery function, inputting their backup phrase accurately. It is imperative to monitor for any unauthorized transactions during this process, and to change passwords associated with email or accounts linked to the wallet for enhanced security. Attention to these details is critical for effective recovery.
Best Practices for Preventing Future Hacks
Implementing robust security measures is essential for preventing future hacks of crypto wallets, as this proactive approach safeguards digital assets against evolving threats. Adhering to best security practices greatly enhances wallet integrity and accessibility. Employing effective wallet encryption methods also fortifies the wallet against unauthorized access.
Key strategies include:
- Two-Factor Authentication (2FA): Adding an extra layer of security through a secondary verification method.
- Regular Software Updates: Ensuring wallet software is consistently updated to patch vulnerabilities.
- Using Cold Storage: Storing cryptocurrencies offline, minimizing exposure to online threats.
- Strong Passwords and Recovery Phrases: Creating complex, unique passwords and safeguarding recovery phrases to prevent unauthorized access.
Exploring Alternatives and Backup Options
In addition to implementing strong security measures, exploring alternative wallets and backup options can greatly enhance the resilience of digital assets against security breaches. Utilizing different recovery methods can provide peace of mind to crypto holders. Below is a table outlining various alternative recovery methods and backup solutions:
| Wallet Type | Features | Recovery Method |
|---|---|---|
| Hardware Wallet | Offline storage, high security | Seed phrase restoration |
| Software Wallet | User-friendly, easily accessible | Cloud backup, encryption |
| Paper Wallet | Physical form, immune to digital hacks | Essential for long-term storage |
| Multisig Wallet | Multiple signatures required for transactions | Distributed backup keys |
| Custodial Wallet | Third-party management, insurance options | Provider backup systems |
These alternatives and backup solutions can effectively mitigate risks associated with wallet hacking.
Frequently Asked Questions
Can a Hacked Wallet Still Be Protected After a Recovery Attempt?
A hacked wallet may regain some protection after recovery, but ensuring wallet security remains vital. Implementing robust security measures is essential for preventing future hacks, thereby safeguarding assets and enhancing confidence in cryptocurrency management.
What Should I Do if I Lost My Recovery Phrase?
If a recovery phrase is lost, exploring recovery options becomes essential. Implementing robust backup strategies, such as securely storing seeds and using hardware wallets, can enhance future security and mitigate risks associated with potential losses.
How Can I Find Out Who Hacked My Crypto Wallet?
Determining a hacker’s identity can be challenging, with only 40% of breaches ever resolved. Utilizing hacker identification methods, individuals should look for wallet breach signs to gather clues and report suspicious activities to authorities.
Are There Specific Tools for Tracking Stolen Cryptocurrency?
There are specific tools for tracking stolen cryptocurrency, including blockchain explorers that allow users to view transaction histories. Additionally, transaction monitoring services can help identify suspicious activities linked to hacked wallets, enhancing recovery chances.
How Does Insurance for Crypto Wallets Work?
Crypto insurance provides wallet protection by covering losses from theft, hacking, or unforeseen breaches. While skeptics may doubt its reliability, such policies offer peace of mind, allowing investors to navigate the volatile crypto landscape with safety.
Conclusion
In summary, while recovering a hacked crypto wallet may seem challenging, applying systematic measures can facilitate the process. By isolating compromised devices, contacting pertinent exchanges, and utilizing backup options, individuals can reclaim access and secure their assets. Ironically, it is often through the misfortunes of a hack that users discover the importance of robust security practices, reminding them that vigilance in digital asset management is not merely a suggestion, but rather a necessity for safeguarding investments in an increasingly perilous landscape.