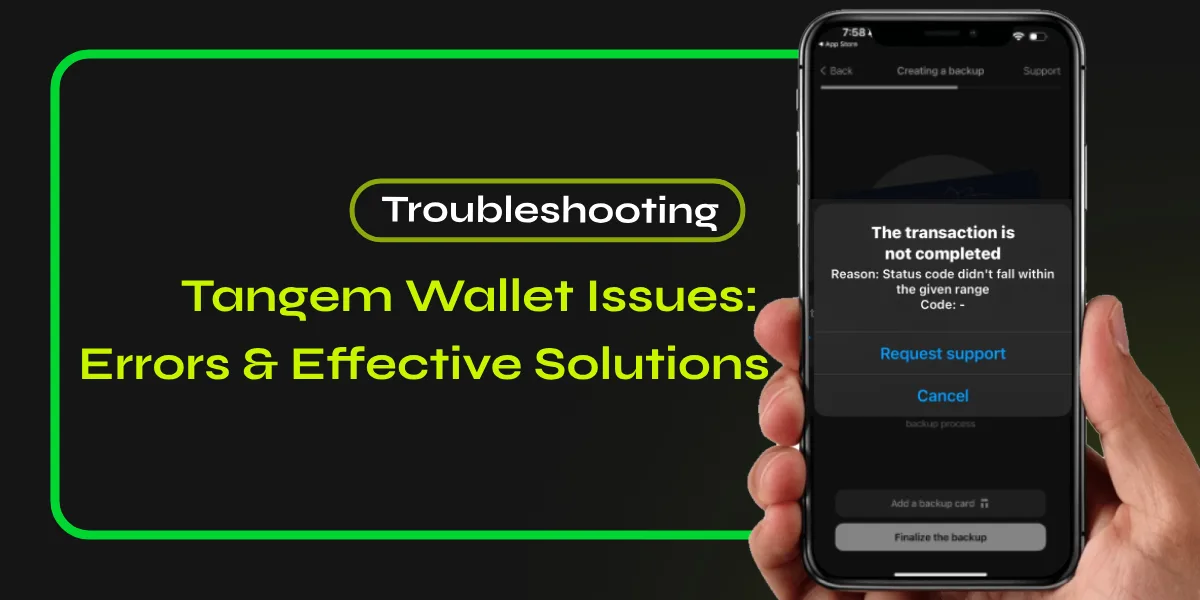
Cold wallets serve as a pivotal solution for securing cryptocurrency investments, providing a safeguard against online threats. Key benefits include enhanced security, offline storage, and protection from hacking attempts. When selecting a cold wallet, considerations such as hardware reliability, firmware update policies, and tamper resistance are critical. Setting up these wallets requires meticulous attention to detail, including secure storage practices for private keys and recovery phrases. The subsequent sections will outline essential steps for effective utilization and protection of these wallets.
Key Takeaways
- Choose a cold wallet with strong security features like encryption and two-factor authentication to protect your private keys.
- Store your cold wallet in a secure, tamper-proof location, away from extreme environmental conditions.
- Regularly back up your wallet information, keeping encrypted copies in multiple secure locations for asset recovery.
- Keep your recovery phrases and passwords in a safe place, accessible only to trusted individuals.
- Stay informed about potential cybersecurity threats, like phishing scams, and adopt best practices for online safety.
Understanding Cold Wallets and Their Benefits
What exactly are cold wallets, and how do they function as secure storage solutions for cryptocurrencies? Cold wallets, or offline storage options, provide a robust alternative to hot wallets, as they remain disconnected from the internet, markedly reducing vulnerability to cyberattacks.
Cold Wallet Advantages:
- Enhanced Security Features: Unlike hot wallets, which store private keys online, cold wallets protect keys in a secure offline environment, utilizing encryption and physical security measures.
- Durability: Many cold wallets are designed to withstand physical damage and unauthorized access.
- User Control: They allow users to retain complete control over their assets, decreasing dependence on third-party exchanges.
Choosing the Right Cold Wallet for Your Needs
Selecting the appropriate cold wallet involves evaluating various features and specifications that align with specific storage needs and individual investment strategies. Critical considerations include:
- Wallet Features: Compatibility with different cryptocurrencies, user interface, and firmware updates.
- Security Types: Encryption methods, two-factor authentication, and backup options.
- Physical Characteristics: Size, portability, and environmental resistance.
- Price Range: Initial cost and ongoing maintenance expenses.
Investors should weigh these factors to determine which cold wallet best safeguards their assets while enhancing usability. A well-chosen wallet not only secures investments against threats but also optimizes the overall management of digital currencies. In-depth research into each model’s strengths and weaknesses will provide a clearer picture, ultimately aiding in informed decision-making.
Setting Up Your Cold Wallet: A Step-by-Step Guide
Setting up a cold wallet involves critical steps that guarantee the secure storage of cryptocurrency assets. First, individuals must select a suitable cold wallet, considering factors such as security features, ease of use, and compatibility with various cryptocurrencies. Following the selection, the next phase requires the secure transfer of funds, which demands adherence to best practices for securing private keys and validating transactions to mitigate the risk of unauthorized access.
Choose Your Cold Wallet
When evaluating the choice of a cold wallet for cryptocurrency storage, one must assess several critical factors that influence both security and usability. It is crucial to examine hardware specifications, wallet compatibility, and additional features to guarantee an excellent choice. Key considerations include:
- Security Features: Look for wallets with robust encryption and PIN protection.
- Supported Cryptocurrencies: Confirm compatibility with a wide range of digital assets that align with the user’s portfolio.
- User Interface: Select wallets that offer intuitive navigation for ease of use.
- Accessibility Options: Reflect on how the wallet allows transactions, such as using USB or wireless connection.
Making an informed decision involves understanding these aspects to secure crypto investments effectively.
Transfer Funds Securely
Transferring funds securely to a cold wallet necessitates a meticulous approach to ascertain that the user’s digital assets remain protected from potential threats. It is essential to ensure that all security protocols are observed throughout the transaction process. Users should initiate transaction monitoring to track the movement of digital assets meticulously and confirm that transfers are completed without intervention.
Key steps include:
- Connect the cold wallet: Use a secure device to establish connectivity.
- Generate a transaction: Create a transaction within the wallet’s interface.
- Verify recipient address: Double-check all addresses for accuracy to avoid errors.
- Securely sign the transaction: Confirm the transaction within the cold wallet, protecting funds security.
- Monitor for confirmation: Wait for confirmations on the blockchain to ensure successful transfer.
Transferring Cryptocurrency to Your Cold Wallet
Transferring cryptocurrency to a cold wallet involves selecting an appropriate storage solution and following a systematic transfer process. Users must consider factors such as security features, compatibility with their preferred cryptocurrencies, and ease of use when selecting a cold wallet, which can include hardware or paper wallets. Once a cold wallet is chosen, the process for transferring cryptocurrency typically entails generating a wallet address, initiating a transaction from the exchange or hot wallet, and ensuring that the transaction is confirmed on the blockchain.
Selecting a Cold Wallet
How does one guarantee the secure transfer of cryptocurrency assets to a cold wallet? The selection of an appropriate cold wallet is critical for safeguarding digital assets. It is vital to assess both hardware options and software comparisons available in the market. Users must consider the following factors when choosing a cold wallet:
- Security Features: Look for wallets with robust encryption protocols.
- User Interface: An intuitive interface can simplify the management of assets.
- Compatibility: Confirm that the wallet supports the desired cryptocurrencies.
- Backup Options: Reliable wallets should offer secure recovery methods for lost access.
Evaluating these aspects will aid investors in making informed decisions, thereby maximizing the security of their cryptocurrency investments.
Transfer Process Steps
A successful transfer of cryptocurrency assets to a cold wallet involves several precise and methodical steps, guaranteeing both the integrity and security of the digital funds. Initially, the user must generate a unique wallet address from the cold wallet. This address is vital for the wallet transfer process, as it directs the digital assets to the appropriate location.
Next, the user accesses their online exchange or hot wallet and selects the option to withdraw or send cryptocurrency. They must input the cold wallet address and specify the amount to transfer.
It is important to double-check all details, as errors can compromise asset security. Finally, the user confirms the transaction, after which they should verify receipt within the cold wallet to confirm successful transfer.
Best Practices for Storing Your Cold Wallet
Regularly implementing best practices for storing a cold wallet is essential for ensuring the security of cryptocurrency investments. Effective wallet management techniques can greatly enhance cold wallet security.
- Physical Security: Store the cold wallet in a secure, tamper-proof location, such as a safe or safety deposit box.
- Environment Control: Keep the storage environment dry and free from extreme temperatures, humidity, or exposure to magnetic fields.
- Access Control: Limit access to the cold wallet by restricting only trusted individuals, ensuring that only authorized users can retrieve it.
- Documentation: Maintain a secure, encrypted record of wallet recovery phrases and passwords, ensuring this information is stored independently of the wallet itself.
Adhering to these practices helps mitigate risks and bolsters the integrity of cryptocurrency assets.
Regularly Updating Your Security Measures
Updating security measures is an essential practice for cryptocurrency investors, particularly those relying on cold wallets, as the evolving landscape of cyber threats necessitates continuous assessment and improvement of protective protocols. Regularly updating software is crucial; outdated systems may harbor vulnerabilities that cybercriminals can exploit. Investors should also prioritize enhancing encryption methods, which fortifies the data integrity of stored cryptocurrencies.
Key actions to contemplate include:
- Schedule frequent software updates: Guarantees the latest protection features are integrated.
- Adopt robust encryption standards: Such as AES-256 to safeguard private keys.
- Conduct routine security audits: Identifies and mitigates potential weaknesses in systems.
Recovering Your Assets: Understanding Backup and Recovery
Maintaining the integrity of one’s cryptocurrency assets requires more than just robust security measures; it necessitates an extensive understanding of backup and recovery strategies. Effective asset recovery hinges on well-implemented backup strategies, which should include:
- Secure Storage: Use multiple physical locations for backups to minimize loss risk.
- Encryption: Encrypt backup files to prevent unauthorized access.
- Regular Updates: Periodically update backups to reflect recent transactions or wallet information.
- Redundancy: Keep at least two copies of backups, stored in different formats (e.g., USB drives, paper printouts).
Educating Yourself on Potential Threats and Scams
How can one effectively safeguard their cryptocurrency investments in an environment rife with potential threats and scams? Educational initiatives focused on scam awareness and threat detection are essential for investors. Understanding various types of scams, including phishing attempts, Ponzi schemes, and fake exchanges, can considerably reduce risks. A robust knowledge base enables investors to recognize red flags and take preventive measures.
| Type of Scam | Red Flags | Prevention Techniques |
|---|---|---|
| Phishing | Unexpected emails, suspicious links | Verify URLs, use bookmarks |
| Ponzi Scheme | Promises of guaranteed returns | Research, read reviews |
| Fake Exchanges | Lack of regulation, poor reviews | Use reputable platforms only |
Awareness leads to informed investments, fostering a more secure crypto environment.
Frequently Asked Questions
Can I Use Multiple Cold Wallets for My Crypto Investments?
Yes, individuals can use multiple wallets for their cryptocurrency investments. Managing assets across various cold wallets enhances security, diversifies risk, and provides easier access to specific funds, ultimately offering better control over one’s digital assets.
How Often Should I Check My Cold Wallet’s Security?
Like a vigilant guardian, one should conduct cold wallet maintenance and security audits regularly, ideally every few months, ensuring that the treasures within remain safe from unseen threats lurking in the shadows of the digital world.
Is It Safe to Buy a Used Cold Wallet?
Buying a used cold wallet can be risky. Ensuring used wallet security depends on verifying cold wallet authenticity. A thorough inspection of the device’s condition and previous ownership history is essential to mitigate potential threats.
What Happens if I Forget My Cold Wallet’s PIN?
Forgetting a cold wallet’s PIN typically results in access loss. Recovery options may include using backup methods, like seed phrases. Without these, retrieving funds becomes exceedingly difficult, underscoring the importance of secure recovery practices.
Can Cold Wallets Store All Types of Cryptocurrencies?
“Variety is the spice of life.” Cold wallets can store multiple cryptocurrency types, but the supported cryptocurrencies depend on the cold wallet types being used. Users should verify compatibility before making their selections to ascertain efficient storage.
Conclusion
To sum up, securing cryptocurrency investments through cold wallets requires a methodical approach that encompasses several critical actions. By selecting a suitable wallet type, adhering to best practices for storage, and implementing regular security updates, investors can bolster their asset protection. Furthermore, maintaining thorough backups and understanding potential threats also play indispensable roles in ensuring the integrity of digital wealth. Ultimately, consistent vigilance and education are paramount in safeguarding against vulnerabilities inherent in the cryptocurrency landscape.