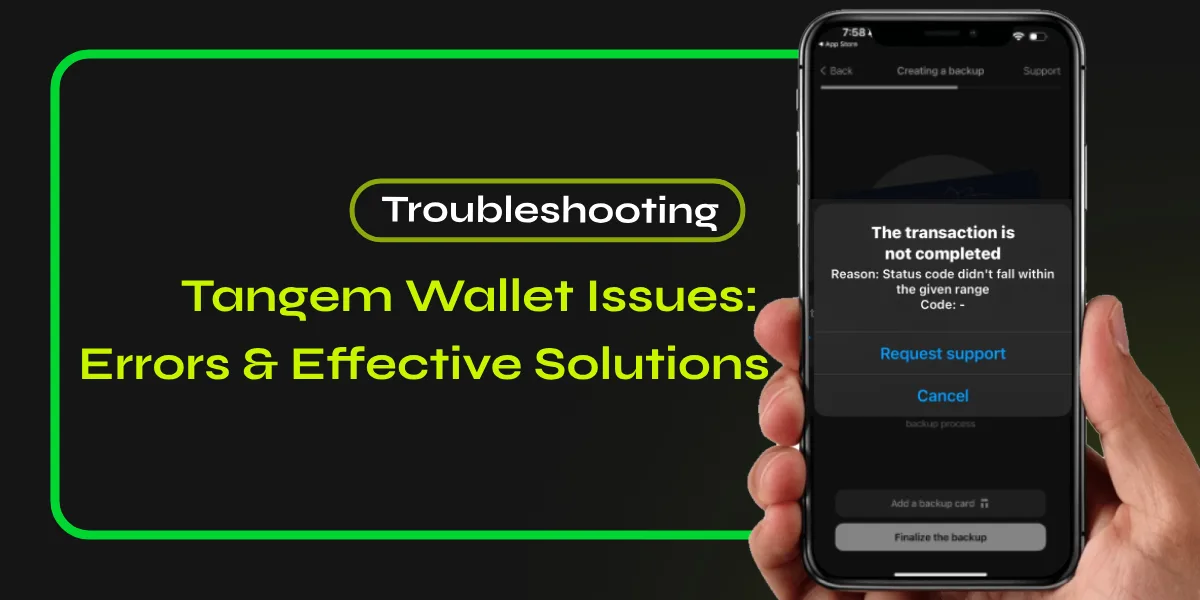
Phishing attacks targeting crypto wallets pose significant risks, necessitating a proactive approach to security. Key strategies include:
- Verifying website URLs for HTTPS adherence and spelling accuracy.
- Implementing two-factor authentication to enhance access security.
- Regularly updating passwords with strong, unique combinations.
Additional vigilance towards unsolicited communications is vital. Awareness of evolving phishing tactics is essential for protecting valuable digital assets. Understanding these principles fosters informed decision-making in safeguarding one’s financial information and assets.
Key Takeaways
- Verify the authenticity of emails and websites by checking domain extensions, HTTPS presence, and ensuring no misspellings in URLs.
- Use two-factor authentication to add an extra layer of security to your cryptocurrency wallet.
- Create strong, unique passwords for each account, and consider using a password manager for better management.
- Be cautious of unsolicited communications asking for sensitive information and avoid engaging with them.
- Report any phishing attempts to relevant authorities and utilize community resources to enhance awareness and safety.
Recognizing Phishing Scams
Phishing scams represent a considerable threat to the security of cryptocurrency wallets, often targeting unsuspecting individuals through deceptive tactics. Recognizing these scams requires vigilance, as they employ various phishing indicators to manipulate victims. Common tactics include:
- Impersonation: Attackers frequently masquerade as reputable services, using logos and branding to lend credibility.
- Urgent language: Phishing messages often create a false sense of urgency, pressuring users to act quickly without thorough verification.
- Suspicious links: Malicious URLs may lead to counterfeit websites designed to harvest sensitive information.
Effective scam recognition involves scrutinizing communication for these indicators, ensuring that individuals maintain a cautious approach when interacting with digital platforms. Awareness of these signs can greatly enhance one’s defense against potential threats targeting cryptocurrency assets.
Checking Website URLs Carefully
How can individuals guarantee the safety of their cryptocurrency transactions when steering through the vast digital landscape? A critical measure involves diligently checking website URLs to assess website legitimacy. A fraudulent site may closely mimic a reputable one, using slight variations in the URL structure.
To navigate safely, users should consider the following guidelines:
- Verify the domain extension: Look for trusted extensions like .com or .org.
- Inspect for HTTPS: Confirm the site employs HTTPS, indicating a secure connection.
- Check for misspellings: Be wary of subtle errors in the URL that may suggest a phishing attempt.
- Use a URL checker: Online tools can validate the authenticity of the website before engaging in transactions.
Adhering to these steps can greatly mitigate the risk of falling victim to phishing scams.
Enabling Two-Factor Authentication
One of the most effective strategies for securing cryptocurrency transactions involves enabling two-factor authentication (2FA), a security measure that adds an additional layer of protection beyond traditional passwords. By implementing multi-factor authentication, users can greatly reduce the risk of unauthorized access. This measure typically requires a second form of verification, often delivered through authentication apps, that generates time-sensitive codes unique to the user’s account.
Key features of 2FA include:
- Reduced Risk: Even if passwords are compromised, an additional verification step is necessary.
- Flexibility: Various authentication apps, such as Google Authenticator or Authy, can be utilized.
- User Control: Users can easily manage and modify their authentication settings.
Keeping Software Up to Date
Maintaining up-to-date software is paramount for safeguarding cryptocurrency wallets against potential cyber threats, as outdated applications may harbor vulnerabilities that attackers could exploit. Regular updates not only enhance functionality but also incorporate critical software vulnerability patches that protect users from emerging threats. Utilizing automated update processes is advisable, ensuring that security measures remain current without manual intervention.
- Regularly check for updates to wallet software.
- Enable automated update processes where available.
- Review release notes for patch details and vulnerability fixes.
- Perform manual updates if automated processes are not feasible.
Avoiding Suspicious Links and Emails
Phishing attacks increasingly target cryptocurrency users, exploiting unsuspecting individuals who unknowingly click on malicious links or download harmful attachments. To mitigate these risks, users must remain vigilant regarding suspicious email sources. Emails that contain unsolicited requests for sensitive information or appear to originate from unofficial addresses can be red flags for potential scams.
Key strategies for avoiding social engineering tactics include:
- Hovering over links before clicking to reveal the actual URL.
- Verifying the sender’s email address by checking for irregularities or inconsistencies.
- Avoiding engagement with emails that prompt urgency or fear, as these are common psychological triggers used by attackers.
- Reporting phishing attempts to appropriate authorities or platforms to help safeguard the community.
Using Secure Password Practices
Using secure password practices is essential for safeguarding crypto wallets against potential phishing attacks. Strong password creation, which involves incorporating a mix of uppercase and lowercase letters, numbers, and special characters, greatly enhances security by making unauthorized access more difficult. Additionally, regular password updates and the utilization of password managers can streamline this process, allowing users to maintain unique, complex passwords for each account while reducing the risk of falling victim to phishing schemes.
Strong Password Creation
A robust password is one of the foundational elements for securing a crypto wallet, as its complexity can considerably reduce the risk of unauthorized access and potential financial loss. Creating strong passwords requires careful consideration of various factors, particularly regarding password length and password complexity.
To enhance password security, one should consider the following practices:
- Minimum Length: Verify the password is at least 12-16 characters long.
- Character Variety: Use a mix of uppercase letters, lowercase letters, numbers, and special symbols.
- Avoid Predictability: Steer clear of easily guessable information like birthdays or common phrases.
- Unique Passwords: Do not reuse passwords across different platforms or accounts.
Implementing these strategies can considerably fortify a crypto wallet against phishing attacks.
Regular Password Updates
Establishing a routine for regular password updates is a critical measure in maintaining the security of a crypto wallet, as it diminishes the likelihood of unauthorized access over time. Users should adhere to a systematic password change frequency, ideally changing passwords every three to six months. Enforcing password policies can further enhance this practice. These policies may include:
- Mandating a mix of upper and lower case letters, numbers, and special symbols.
- Encouraging the avoidance of easily guessable information, such as birthdays or pet names.
- Requiring unique passwords for different accounts to limit vulnerability in case of a breach.
Password Manager Benefits
Password managers offer numerous advantages that greatly enhance secure password practices for individuals managing crypto wallets. By utilizing various password manager options, users can efficiently organize their passwords, ensuring both accessibility and security. Key password manager features contribute to an optimized user experience, safeguarding sensitive information.
- Automated Password Generation: Creates complex and unique passwords for each account.
- Encrypted Storage: Safeguards passwords using advanced encryption algorithms, preventing unauthorized access.
- Cross-Platform Synchronization: Allows users to access their passwords securely across multiple devices.
- Two-Factor Authentication Support: Enhances account security by requiring an additional verification step.
These functionalities not only streamline password management but also bolster overall security, dramatically reducing the likelihood of falling victim to phishing attacks.
Educating Yourself About Common Tactics
How can users effectively safeguard their crypto wallets from phishing attacks? Understanding common tactics employed by attackers is essential for effective protection. Phishing psychology often leverages social engineering tactics to manipulate victims into providing sensitive information. Users should familiarize themselves with the following:
- Email Spoofing: Attackers may use fake email addresses that closely resemble legitimate sources.
- Urgency Induction: Messages that create a false sense of urgency compel users to act quickly, bypassing caution.
- Fake Websites: Sophisticated replicas of official sites designed to harvest login credentials or private keys.
Reporting Phishing Attempts
Recognizing phishing attempts is essential for safeguarding one’s crypto wallet, as failure to identify these threats can result in significant financial loss. Various reporting channels exist, including dedicated cybersecurity platforms, governmental organizations, and social media networks, facilitating the timely documentation of suspicious activity. Prompt reporting not only aids in the prevention of future attacks but also contributes to broader efforts in combating cybercrime, highlighting the collective responsibility of all users to maintain a secure digital environment.
Identifying Phishing Attempts
In what ways can individuals effectively discern phishing attempts targeting their cryptocurrency wallets? Recognizing phishing indicators is essential to safeguard digital assets. To evaluate email authenticity and identify potential scams, individuals should consider the following aspects:
- Look for misspellings, grammatical mistakes, and awkward phrasing in the email.
- Verify the sender’s email address against known legitimate addresses of the cryptocurrency service.
- Check for unsolicited requests for sensitive information, such as passwords or private keys.
- Hover over links to inspect URLs before clicking, ensuring they direct to secure and authentic domains.
Reporting Channels Available
When individuals encounter a phishing attempt targeting their cryptocurrency wallet, they may wonder what steps are available for reporting such fraudulent activities. Various reporting mechanisms exist to address these incidents effectively, enabling users to alert the appropriate entities. Key channels include:
- User Organizations: Many cryptocurrency platforms and wallet providers have dedicated support teams for reporting phishing attempts. Users should consult their service provider’s guidelines on reporting.
- Anti-Phishing Websites: Numerous organizations maintain resources for documenting and disseminating phishing scams, which can help others avoid similar traps.
- Regulatory Agencies: Users can report fraudulent activities to local financial authorities or law enforcement agencies, which may investigate further.
Utilizing these channels can enhance community safety and awareness regarding phishing threats.
Importance of Timely Reporting
Timely reporting of phishing attempts is critical not only for individual victims but also for the broader cryptocurrency community, as prompt action can mitigate ongoing threats and prevent further incidents. Effective communication and timely notifications regarding phishing activities enable developers and service providers to respond swiftly, fostering a safer online environment.
The significance of timely reporting includes:
- Mitigating Ongoing Threats: Reducing the window of opportunity for attackers.
- Enhancing Community Awareness: Informing other users about the potential risks.
- Assisting in Investigations: Providing essential information to authorities for action.
- Strengthening Security Systems: Facilitating updates and patches to prevent future incidents.
Engaging in proactive reporting not only safeguards individual assets but also fortifies the integrity of the cryptocurrency ecosystem.
Frequently Asked Questions
What Should I Do if I Fall for a Phishing Scam?
Upon falling for a phishing scam, one should act quickly by reporting scams to authorities and financial institutions. Exploring recovery options is vital, including freezing accounts and seeking assistance from cybersecurity professionals for potential recovery measures.
Are Hardware Wallets Safe From Phishing Attacks?
Hardware wallets boast impressive security, often mocking phishing attempts from their digital thrones. Yet, even these fortresses are not immune; users must remain vigilant, blending hardware wallet security with proactive phishing attack prevention for ideal defense.
Can Antivirus Software Help Prevent Phishing?
Antivirus software can enhance security through phishing detection, providing users with alerts about suspicious websites and emails. However, its effectiveness varies, and it should complement, not replace, vigilant personal habits for best protection.
How Often Should I Change My Wallet Password?
Research shows that 81% of data breaches involve weak passwords. To guarantee ideal password longevity and complexity, experts recommend changing wallet passwords every three to six months, thereby enhancing security and reducing vulnerability to attacks.
Are Public Wi-Fi Networks Safe for Crypto Transactions?
Public Wi-Fi networks pose significant risks for crypto transactions due to potential interception. Users should prioritize secure browsing practices, such as utilizing Virtual Private Networks (VPNs) and avoiding sensitive activities on unsecured connections to safeguard their assets.
Conclusion
In summary, safeguarding a crypto wallet against phishing attacks necessitates a multifaceted approach, encompassing both technological measures and personal vigilance. By consistently verifying URLs, employing two-factor authentication, and maintaining current software, users can greatly reduce their risk. Additionally, recognizing unsolicited communications and adhering to secure password practices further enhances security. As phishing tactics continually evolve, ongoing education about emerging threats proves vital; by remaining informed, individuals fortify their defenses and enhance the protection of their digital assets.