By Ryan Mitchell | Updated: December 4, 2025
- Update Log: Added comparison of new metal storage solutions for 2025 & expanded hardware wallet recovery protocols.
Editor’s Note:
“I’ve spent years analyzing how people lose their crypto, and the reality is harsh: it’s rarely a sophisticated hack, but simple negligence with their seed phrase. Users often underestimate the fragility of paper backups or the persistence of digital footprint scanners. This guide isn’t just advice; it’s a mandatory protocol for anyone serious about being their own bank.”
— Ryan Mitchell, Technical Lead at BeginnerWallets
Your seed phrase is the master key to your digital wealth, acting as the only way to regain access to your crypto if your device is lost or damaged. To ensure your crypto assets remain safe, you must record your seed phrase on a physical medium like a metal backup or piece of paper, store it in a secure location, and never create a digital copy or share it with anyone.
Understanding Your Seed Phrase
A seed phrase, also known as a recovery phrase or mnemonic phrase, is a list of words (usually 12 or 24 words) generated when you set up a new crypto wallet. This list of 2048 words comes from the BIP-39 standard and translates into your private key, which controls your funds on the blockchain.
Understanding seed phrases and private keys is fundamental to crypto safety. Your wallet doesn’t actually store your coins; it stores the keys that allow you to move them. Therefore, your seed phrase acts as the ultimate backup. If you lose access to your hardware device or phone, simply input your seed phrase into a new compatible wallet to restore your funds. However, if your seed phrase is lost, your money is gone forever. This is why keeping your seed phrase secure is the single most important task for any investor.
Best Ways to Store Your Seed Phrase
How you store a seed phrase determines the security level of your digital assets. While a piece of paper is the most common method for backing up your seed phrase, it is vulnerable to fire and water damage.
Storage Method Comparison
| Storage Method | Security Level | Cost | Recommended Status |
|---|---|---|---|
| Paper Backup | Low (Vulnerable to fire/water) | Low | Temporary only |
| Metal Backup | High (Fire/Water/Impact resistant) | Medium ($20-$100) | Highly Recommended |
| Digital/Cloud | Unsafe (Hackable) | Free | NEVER |
| Hardware Wallet | Very High (Offline generation) | High ($60+) | Essential |
- Metal Backup: For long-term security, we recommend using a metal seed storage solution. Engraving your 24 word seed onto a steel plate protects it from fire, water, and physical degradation.
- Safe Deposit Box: Storing a copy of your seed phrase in a safe deposit box at a bank adds an extra layer of physical security, keeping it away from home burglaries.
- Secure Location: If keeping it at home, ensure your seed phrase is hidden in a secure place like a hidden safe.
- Multiple Copies: Consider keeping copies of your seed phrase in geographically separate locations to protect against natural disasters.
Best practices dictate that you must never store your seed phrase on a computer, phone, or cloud storage. Hackers constantly scan for files containing words like “seed”, “recovery”, or “secret”. A digital copy or photo of your seed phrase creates a massive vulnerability.
Hardware Wallets and Seed Security
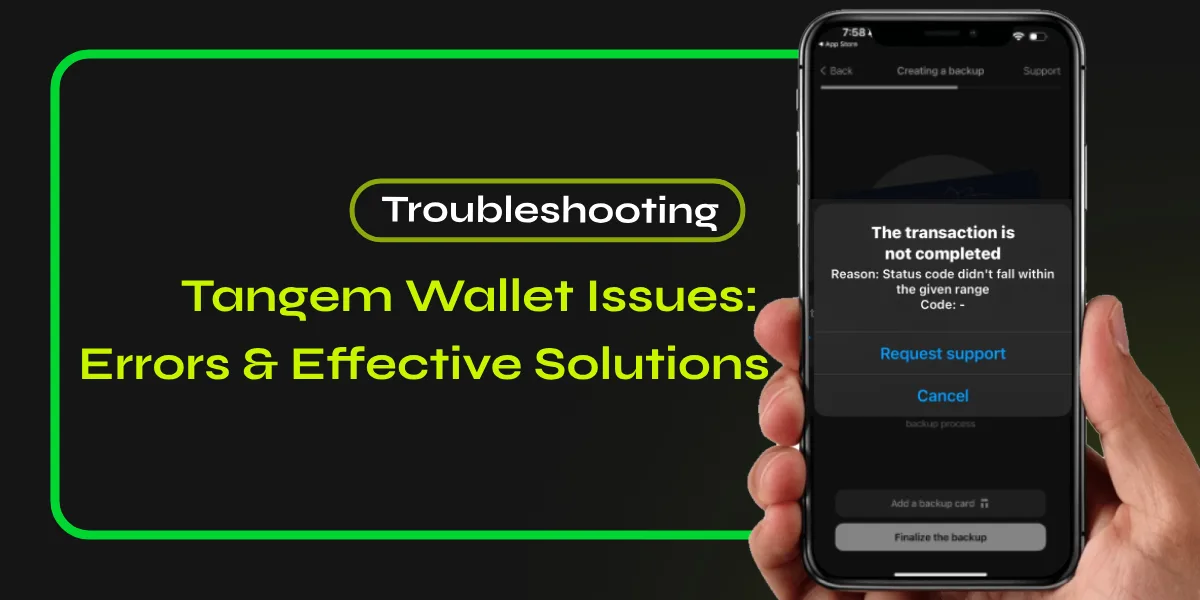
A hardware wallet, such as a Ledger device or Tangem, offers the highest standard of security for your crypto. When you initialize a hardware wallet, the seed phrases are generated offline within the device’s secure element. This ensures your private key never touches the internet, making it nearly impossible to hack remotely.
If you are exploring card-shaped cold wallets, you might wonder: is Tangem Wallet safe?. Like Ledger, it uses a secure chip to protect your keys, but the form factor is different. For those interested in spending crypto directly, understanding features like Tangem Pay is also useful, but always prioritize base-layer security first.
- Ledger: A Ledger wallet isolates your seed phrase from malware and viruses on your computer.
- Cold Storage: By keeping your seed offline, you ensure that access to your wallet requires physical confirmation on the device.
- Wallet Provider: Choose a reputable wallet provider that uses open-source standards, allowing you to recover your funds even if the company goes out of business.
Using a hardware wallet is one of the best ways to protect your seed phrase. Even if your computer is compromised, your crypto assets remain safe because the transaction signing happens inside the device.
Critical Risks: Never Share Your Seed Phrase
The golden rule of crypto is simple: Never share your seed phrase with anyone. No legitimate support team, including Ledger support or any wallet provider, will ever ask for your seed phrase. If anyone with your seed phrase gains access, they can immediately transfer all your funds to their own wallet.
- Phishing Attacks: Scammers create fake websites asking you to input your seed phrase to “verify” or “unlock” your account.
- Social Engineering: Be wary of anyone offering to help you regain access to your crypto who asks for your 12 or 24 words.
- Trust: Even sharing your phrase with anyone you trust is risky. Relationships change, and their security practices might be poor.
Securing your seed phrase means keeping it strictly confidential. Your seed phrase allows total control; therefore, protecting your seed phrase equates to protecting your financial future.
Recovery and Redundancy
If you suspect your seed phrase has been exposed, you must act immediately. Create a new wallet with a new seed phrase and transfer your funds instantly. Do not wait.
To prevent losing access to your digital wealth, verify your backup seed phrase regularly. Some users perform a “dry run” by resetting their wallet (only after ensuring they have the seed phrase verified) to confirm they can restore it. Whether you use a 24 words or 12 or 24 word system, the importance of seed phrases cannot be overstated. They are the barrier between you and irreversible loss.
By following these best practices, such as using a metal seed phrase backup and a hardware wallet, you ensure your crypto journey remains profitable and secure. Remember, in the world of crypto, you are your own bank, and keeping your seed phrase secure is your primary responsibility.
Security Checklist: Are You Safe?
Don’t just read—act. Follow these steps to audit your current setup:
- Verify Offline: Ensure your seed phrase is stored on paper or metal, never in a digital file or photo.
- Test Recovery: If you have a spare device, try to restore your wallet using your seed phrase to verify it works.
- Secure Location: Check that your backup is in a fire-resistant location or a safe deposit box.
- Hardware Check: Confirm you are using a hardware wallet like Ledger or Tangem for long-term storage.
Frequently Asked Questions (FAQ)
Is a 12 or 24 word seed phrase better?
Generally, a 24 word seed phrase offers a higher level of entropy (security) than a 12-word phrase, making it harder to brute-force. However, both are considered secure for most users.
What if I lose my hardware wallet?
As long as you have your seed phrase, your funds are safe. You can buy a new device and input your seed phrase to regain access.
Can I change my seed phrase?
You cannot “change” a seed phrase for an existing wallet. You must generate a new seed phrase by setting up a fresh wallet and transferring your funds to the new addresses.
Is it safe to store a seed phrase in a password manager?
No. Password managers are connected to the internet. For true security, keep your seed phrase offline on a physical medium.
About the Author
Ryan Mitchell serves as the Technical Lead and Security Researcher at BeginnerWallets. With a deep background in FinTech cybersecurity, Ryan specializes in deconstructing hardware wallet architecture and stress-testing recovery protocols. He is known for his “zero-trust” philosophy, rigorously auditing manufacturer claims to ensure users receive only the most battle-tested security advice. When he’s not auditing code, he’s teaching beginners how to secure their digital legacy.