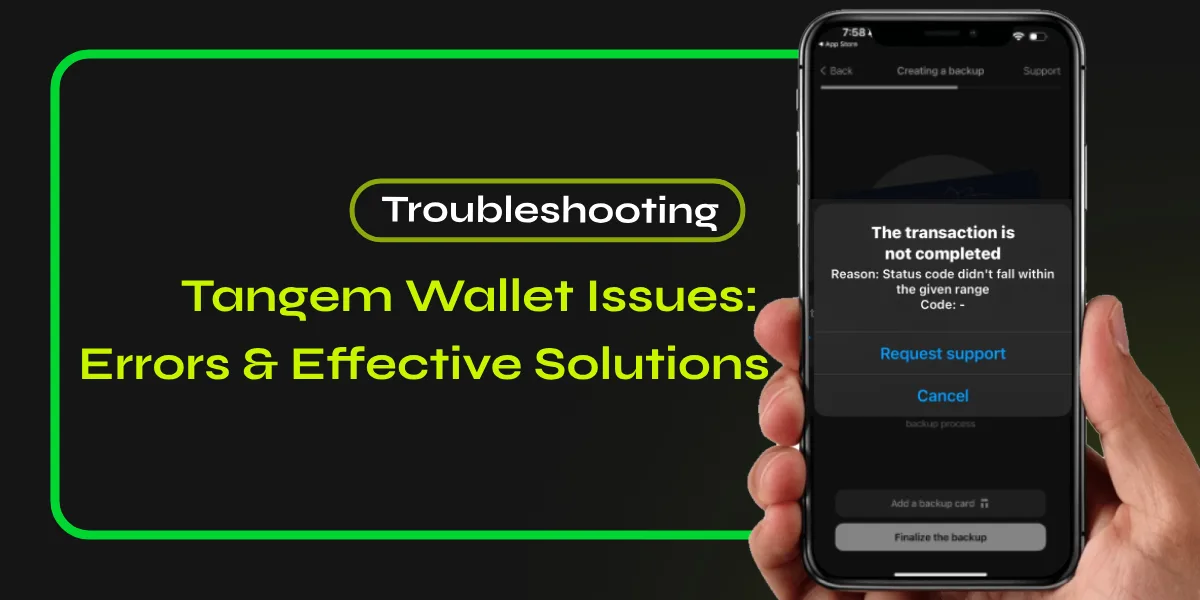
Protecting a crypto wallet requires adherence to established security practices, as vulnerabilities can lead to irreversible financial loss. Key measures include:
- Utilizing hardware wallets, which store private keys offline, mitigating the risk of hacking.
- Enabling two-factor authentication, adding a secondary verification step.
- Regularly updating wallet software to address emerging threats.
- Staying alert for phishing attempts by scrutinizing URLs and sender addresses.
- Backing up wallets and private keys securely to prevent loss.
These practices form a critical foundation for maintaining wallet security.
Key Takeaways
- Use hardware wallets to store private keys offline, providing enhanced protection from hacking and malware threats.
- Enable two-factor authentication (2FA) to add an extra security layer against unauthorized access to your wallet.
- Regularly update your wallet software to ensure you benefit from the latest security patches and features.
- Be vigilant against phishing attempts by verifying URLs and sender email addresses before taking action on communications.
- Backup your wallet and private keys securely, utilizing encrypted storage and creating multiple physical copies in safe locations.
Use Hardware Wallets for Enhanced Security
Utilizing hardware wallets represents a pivotal advancement in the domain of cryptocurrency security. These specialized devices offer robust protection against hacking and malware threats, primarily by storing private keys offline. In the security feature comparison of various hardware wallet options, several key elements stand out:
- Firmware Security: Regular updates to mitigate vulnerabilities.
- User Authentication: PIN codes and biometric security measures.
- Backup and Recovery: Seed phrases for restoring access.
- Multi-Currency Support: Compatibility with numerous cryptocurrencies.
- Physical Security: Encrypted chip technology to prevent unauthorized access.
Thorough analysis of hardware wallet options reveals that, while some prioritize user-friendliness, others focus solely on advanced security protocols. As a result, users can select the most suitable option based on their security needs and cryptocurrency management preferences.
Enable Two-Factor Authentication
Two-factor authentication (2FA) greatly enhances the security of cryptocurrency wallets by adding an extra layer of protection against unauthorized access. This process typically requires users to provide two forms of identification before gaining access to their accounts.
- Methods of 2FA include:
- SMS Verification: Involves receiving a text message with a code that must be entered to proceed.
- Authenticator Apps: These apps generate time-sensitive codes that enhance security by making each login unique.
Implementing 2FA considerably reduces the risk of hacking, as it guarantees that even if a password is compromised, an additional verification method is required to access the wallet. Consequently, users are strongly advised to enable 2FA to safeguard their digital assets effectively.
Regularly Update Software and Wallets
Regularly updating software and wallets is a critical practice that guarantees ongoing protection against emerging threats and exploits in the rapidly evolving cryptocurrency landscape. These updates not only enhance security features but also improve software compatibility and wallet interoperability, ensuring users can effectively manage multiple currencies and platforms without hindrance.
Key benefits of regular updates include:
- Enhanced Security:Integration of the latest security patches to defend against vulnerabilities.
- Increased Functionality: Addition of new features that streamline user experience and transaction efficiency.
- Compatibility Assurance: Ensuring the wallet syncs properly with various blockchain networks and exchanges.
Be Wary of Phishing Attempts
Phishing attempts represent a significant threat within the domain of cryptocurrency, necessitating vigilant awareness among users. Cybercriminals often employ deceptive emails, websites, or messages designed to trick individuals into divulging sensitive information, such as private keys or recovery phrases.
To effectively recognize phishing:
- Examine URLs carefully, noting discrepancies or unusual characters.
- Verify sender email addresses against known contacts or official sources.
- Be cautious of unsolicited communication that demands immediate action.
Users should also educate themselves on common phishing tactics, including fake giveaways and impersonation of legitimate platforms. Importantly, once any phishing attempt is identified, users must report scams to relevant authorities or platforms promptly, contributing to a broader effort to mitigate these threats within the cryptocurrency ecosystem.
Backup Your Wallet and Private Keys
For anyone maneuvering the complexities of cryptocurrency management, ensuring the security of a wallet and its associated private keys is paramount. A thorough backup strategy is essential for effective wallet recovery, which safeguards assets against loss due to hardware failure or human error.
Key components of robust private key management include:
- Secure Storage: Private keys should be kept offline in hardware wallets or encrypted USB drives.
- Multiple Copies: Create several physical copies of the key and store them in different, secure locations.
- Redundancy Protocol: Implement a recovery plan that details procedures for accessing funds if keys are compromised.
- Encryption Techniques: Use strong algorithms to encrypt backups, minimizing the risk of unauthorized access.
Frequently Asked Questions
What Types of Hardware Wallets Are Available on the Market?
Various hardware wallets are available on the market, including the Trezor Model, known for its user-friendly interface and security features, and the Ledger Nano, favored for its robust design and wide compatibility with cryptocurrencies.
How Do I Choose a Reliable Two-Factor Authentication App?
When Jane faced unauthorized access attempts, she explored authentication methods and app comparisons. A reliable two-factor authentication app should offer strong encryption, user reviews, and compatibility with various platforms, ensuring enhanced security against potential cyber threats.
What Software Updates Should I Prioritize for My Wallet?
Prioritizing updates for wallet software should focus on security patches, user interface improvements, and compatibility enhancements. Regular update frequency guarantees protection against vulnerabilities and maintains peak performance, safeguarding the integrity of cryptocurrency holdings.
How Can I Recognize a Phishing Attempt Quickly?
To recognize a phishing attempt quickly, one should be alert for phishing signs like unsolicited emails, misspellings, and requests for sensitive information. Avoid clicking on fraudulent links, which often lead to deceptive websites aiming to steal credentials.
Where Is the Safest Place to Backup My Private Keys?
Secure storage solutions, like safely storing paper wallets in fireproof safes, or utilizing encrypted storage methods, bolster protection against potential breaches and guarantee private keys remain confidential, contributing to thorough crypto asset security strategies.
Conclusion
In summary, adopting a multifaceted approach to securing a crypto wallet is paramount for safeguarding digital assets. By employing hardware wallets, users can guarantee their private keys remain inaccessible to cyber threats. Two-factor authentication provides an additional barrier against unauthorized access, while regular software updates fortify defenses against vulnerabilities. Vigilance against phishing attempts and maintaining encrypted backups further enhances security measures. Ultimately, these essential practices converge to establish a robust protective framework for any cryptocurrency holder.