Setting up a cryptocurrency hardware wallet is essential for safeguarding digital assets. This process requires specific steps to guarantee the device’s operational efficiency and security. Key elements of setup include:
- Device Verification: Confirm all components are present, including cables and manuals.
- Software Installation: Download the official wallet software to your computer.
- Security Measures: Create a complex PIN and generate a recovery seed for account recovery.
Understanding these steps paves the way for effectively managing and protecting assets in this rapidly evolving digital environment.
Key Takeaways
- Unbox your hardware wallet carefully, ensuring all components are included and the device is free from physical damage before setup.
- Download and install software from the manufacturer’s official website, updating the firmware for optimal security and compatibility.
- Create a strong PIN and generate a recovery seed, securely storing them offline to protect against unauthorized access and loss.
- Verify your wallet address before funding to prevent mistakes, and choose reputable exchanges for secure cryptocurrency transfers.
- Regularly monitor your wallet for suspicious activity and install security updates to maintain ongoing protection for your digital assets.
Understanding Hardware Wallets and Their Benefits
Hardware wallets represent a sophisticated solution for securely storing cryptocurrencies, distinguishing themselves from software wallets through their intrinsic isolation from internet connectivity. These devices come in various hardware wallet types, including USB sticks and dedicated handheld units, each offering distinct user experiences tailored for different needs.
Key benefits of hardware wallets include:
- Enhanced Security: Private keys are stored offline, reducing exposure to online threats.
- Recovery Options: Most models allow for secure recovery phrases, safeguarding assets during loss or damage.
- Compatibility: They support multiple cryptocurrencies, providing versatility for diverse portfolios.
- User Interface: Many devices feature screens for easy transaction verification.
These features collectively underscores the advantages of employing hardware wallets for cryptocurrency enthusiasts seeking maximum protection and usability.
Choosing the Right Hardware Wallet for Your Needs
When selecting a hardware wallet, individuals must consider several critical factors to guarantee their choice meets their specific needs. Key considerations include a comparison of security features, an overview of supported cryptocurrencies, and an assessment of the price range, as these elements greatly influence both functionality and protection. By thoroughly evaluating these aspects, users can make an informed decision that enhances their cryptocurrency management experience.
Security Features Comparison
Selecting the appropriate hardware wallet necessitates a careful evaluation of various security features designed to protect cryptocurrency assets from unauthorized access and potential threats. Hardware wallet comparisons help consumers identify essential specifications like secure chip technology, backup and recovery options, and user experience reviews to assess usability.
| Feature | Wallet A | Wallet B |
|---|---|---|
| Secure Element | Yes | Yes |
| 2-Factor Authentication | Yes | No |
| Biometric Access | No | Yes |
| Recovery Seed Phrase | 24 words | 12 words |
| Open Source | Yes | No |
Understanding these security elements can guide users in selecting a hardware wallet appropriate for their needs and risk anagement preferences.
Supported Cryptocurrencies Overview
Choosing the right hardware wallet requires an understanding of the variety of cryptocurrencies each device supports, as this compatibility directly affects consumers’ ability to manage and secure their digital assets. Various hardware wallets cater to different market trends by offering support for a plethora of cryptocurrencies, including:
- Bitcoin
- Ethereum
- Litecoin
- Ripple
- Cardano
These supported cryptocurrencies are vital for users who wish to diversify their portfolios. Moreover, some wallets may support dozens of altcoins, providing flexibility as new cryptocurrencies emerge in the market. It is essential for potential buyers to assess their individual needs and the specific cryptocurrencies they wish to store, as this will guide them in selecting a hardware wallet that best aligns with their investment strategy and future requirements.
Price Range Assessment
The price of hardware wallets varies considerably based on several factors, including the manufacturer, features, and supported cryptocurrencies. A cost analysis reveals that entry-level options typically range from $50 to $100, while advanced models with enhanced security features can reach up to $300 or more.
When selecting a hardware wallet, budget planning is essential to guarantee proper alignment with financial capabilities and security requirements. Key features influencing price include:
- Supported cryptocurrencies: More options generally equate to higher costs.
- Security features: Biometric authentication and tamper-proof designs often increase expenses.
- User interface: Devices with intuitive navigation may be priced higher.
Potential buyers should meticulously assess their priorities to facilitate informed purchasing decisions, assuring both security and usability needs are met.
Unboxing and Setting Up Your Hardware Wallet
Upon receiving a cryptocurrency hardware wallet, it becomes crucial to carefully unbox and configure the device to guarantee high-quality security and functionality. The initial unboxing experience should be approached methodically, ensuring that all components are accounted for. Typically, the package includes the hardware wallet, a USB cable, and documentation.
During the first setup, users should take note of the following steps:
- Inspect the device for any physical damage.
- Review accompanying manuals for specific instructions.
- Locate the recovery seed kit, essential for wallet recovery.
Care should be taken to keep the recovery seed secure and private, as it is imperative for accessing funds in case of device loss. Confirm that all materials are intact before proceeding further.
Installing the Wallet’s Software and Firmware
The process of installing the wallet’s software and firmware is essential to ensuring best security and functionality for the hardware wallet. Users must first download the appropriate software from the manufacturer’s official website, ensuring it matches the model of the wallet. Following the installation, it is imperative to update the firmware to the latest version, as manufacturers frequently release updates that enhance security features and resolve potential vulnerabilities.
Downloading the Software
Initiating the process of securing cryptocurrency assets requires careful attention to the installation of relevant software and firmware for the selected hardware wallet. Users must prioritize software compatibility with their operating systems to guarantee peak performance and a seamless user interface experience.
| Feature | Description | Importance |
|---|---|---|
| Software Compatibility | Must support Windows, Mac, Linux | Guarantees proper functionality |
| User Interface | Intuitive layout, easy navigation | Enhances user experience |
| Updates | Regular patches for security | Essential for asset protection |
| Security Protocols | End-to-end encryption | Safeguards sensitive information |
Updating the Firmware
Updating the firmware of a cryptocurrency hardware wallet is an essential step in maintaining the device’s security and functionality, as it guarantees that users benefit from the latest features, enhancements, and security protocols. Firmware updates often address vulnerabilities, improve performance, and introduce compatibility with new cryptocurrencies.
The importance of updates cannot be overstated; outdated firmware may leave the wallet exposed to potential exploits. Users should:
- Regularly check the manufacturer’s website for the latest updates
- Follow step-by-step instructions provided by the manufacturer for installation
- Guarantee a secure and stable internet connection during the update process
- Back up wallet data before initiating an update
Creating a Secure PIN and Recovery Seed
Establishing a secure PIN and recovery seed is essential for safeguarding a cryptocurrency hardware wallet, as these elements play a significant role in protecting digital assets from unauthorized access and potential loss. During pin creation, users should opt for a complex combination of numbers, avoiding easily guessed sequences such as birthdays or simple patterns. Typically, a PIN length of at least six to eight digits is recommended.
When it comes to seed management, a recovery seed, often consisting of 12 to 24 randomly generated words, serves as a crucial backup for wallet recovery. Users must document this recovery seed securely, ensuring it is stored offline, away from potential theft or damage. Proper handling of both PIN and recovery seed is crucial in maintaining asset security.
Backing Up Your Recovery Seed Safely
Backing up a recovery seed is critical for guaranteeing access to cryptocurrency assets in the event of hardware failure or loss. Secure storage methods can vary but often include options such as fireproof safes, safety deposit boxes, and encrypted digital files, each providing different levels of protection against physical and digital threats. Regular checks of these backups are essential to confirm their integrity, as well as to guarantee that they remain accessible and usable when needed.
Importance of Recovery Seed
The recovery seed serves a critical role in the security and accessibility of cryptocurrency holdings, as it enables users to restore or access their wallets in the event of loss, theft, or failure of the hardware wallet. Understanding recovery seed significance and implementing effective recovery seed management is essential for safeguarding digital assets.
| Aspect | Importance |
|---|---|
| Recovery Seed Length | Typically 12-24 words |
| Purpose | Wallet restoration |
| Security Risk | Loss or exposure can lead to asset theft |
| Storage Recommendations | Keep in a secure, offline location |
| Access Protocol | Required for wallet recovery |
Secure Storage Methods
To guarantee the security of a recovery seed, practitioners can employ a variety of secure storage methods that reduce the risk of loss or unauthorized access. Among the most effective strategies is the use of cold storage, which involves storing recovery seeds offline, thereby protecting them from online threats. Various techniques include:
- Physical Copies: Writing the seed on durable materials, such as stainless steel, which resist fire and water damage.
- Multi-Signature Wallets: Utilizing wallets requiring multiple private keys for access, enhancing security by distributing risk across different parties.
- Safety Deposit Boxes: Storing backup documents in secure locations adds another layer of protection against theft or accidental loss.
Regular Backup Checks
Verifying regular backup checks greatly enhances the security and accessibility of a recovery seed, as consistent verification prevents potential data loss and mitigates risks associated with forgotten or deteriorating storage methods. Establishing a backup frequency—whether monthly, quarterly, or annually—guarantees that the recovery seed remains secure and retrievable over time. Users should consider multiple recovery options, such as encrypting backups and storing them in different physical locations, to improve security. Additionally, documenting the process of retrieval can considerably simplify recovery efforts if access is needed. Regular checks also involve testing the integrity of the backup medium to confirm it remains functional. This diligent approach ultimately contributes to the longevity and reliability of cryptocurrency investments, safeguarding against unforeseen circumstances.
Funding Your Hardware Wallet With Cryptocurrency
While many users may be enthusiastic to start utilizing their newly acquired hardware wallet, funding this secure device with cryptocurrency requires a systematic approach that guarantees the safe transfer of digital assets. Users must be diligent in understanding the crypto transfer process, implementing effective funding strategies to verify their investments are secure.
Key considerations include:
- Verifying wallet address: Verify the address is correct to prevent loss of funds.
- Choosing cryptocurrencies: Select which digital assets to transfer based on personal investment strategies.
- Evaluating transaction fees: Consider fees associated with each transfer to optimize costs.
- Utilizing secure exchanges: Opt for reputable exchanges to minimize risks during the funding process.
Managing and Sending Cryptocurrency With Your Wallet
Once funding of the hardware wallet is complete, the process of managing and sending cryptocurrency becomes paramount for users seeking to effectively utilize their digital assets. Users can navigate through their wallet’s interface to view accounts, transaction history, and balances. When sending transactions, it is essential to input the recipient’s address accurately, select the cryptocurrency type, and specify the amount. Users must also consider transaction fees, which vary based on network congestion and the urgency of the transaction. Often, wallets provide customizable fee options, allowing users to select standard, priority, or economy fees. It is advisable for users to double-check transaction details before confirming, ensuring accuracy and security in every transfer, thereby maintaining efficient management of their cryptocurrencies.
Ensuring Ongoing Security for Your Hardware Wallet
A robust strategy for securing a hardware wallet is essential given the potential risks associated with managing cryptocurrency assets. Users should employ ongoing vigilance and proactively implement measures to enhance their wallet’s security. This includes routine checks and updates, with a focus on recognizing vulnerabilities.
- Regularly install security updates provided by the hardware wallet manufacturer.
- Utilize strong, unique PIN codes and passphrases to protect device access.
- Maintain a secure backup of the seed phrase in a safe and offline location.
- Monitor accounts for any suspicious activity or unauthorized transactions.
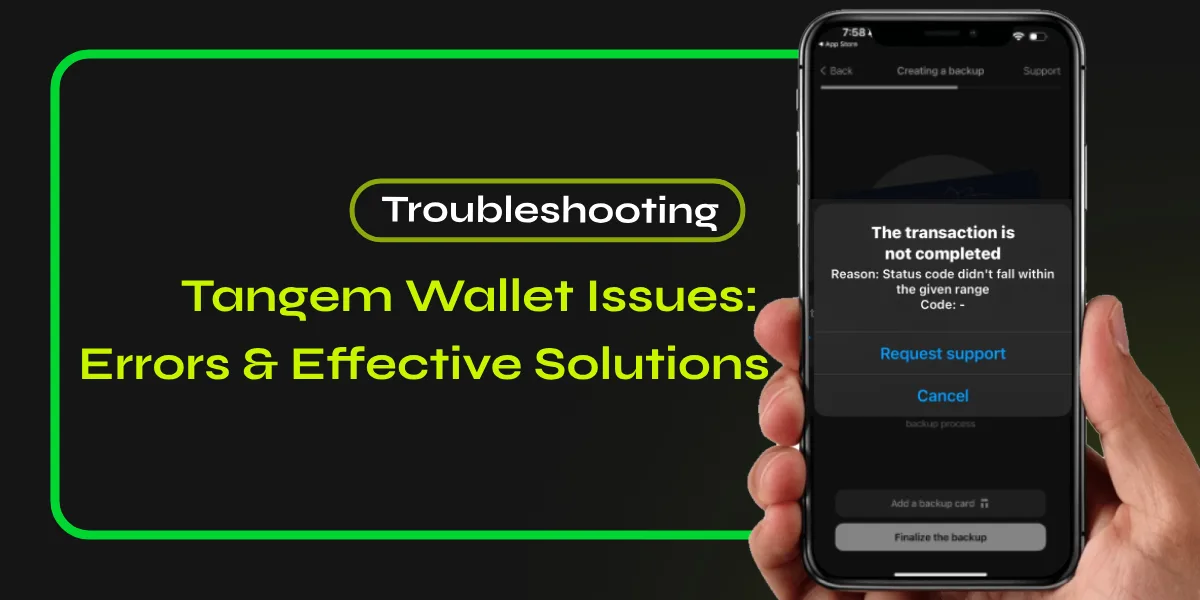
Troubleshooting Common Issues With Hardware Wallets
Despite rigorous security measures, users may occasionally encounter issues with their hardware wallets that can hinder access to their cryptocurrency assets. Common troubleshooting steps include verifying that the device’s firmware is up to date, ensuring the USB connection is secure, and checking for software compatibility. Hardware wallet errors can also arise from incorrect PIN entry, requiring a careful review of the recovery phrase if the wallet becomes inaccessible. Users should consult the manufacturer’s support documentation for specific guidance on error codes and potential fixes. Additionally, regularly backing up wallet data enhances recovery options in case of device failures. Understanding these issues and their resolutions fosters a smoother user experience while safeguarding digital assets against potential loss.
Frequently Asked Questions
What Happens if I Lose My Hardware Wallet?
If one loses a hardware wallet, they potentially lose access to their cryptocurrencies. However, with a proper backup and recovery phrase, the individual can recover their funds and restore access to their wallet securely.
Can I Use a Hardware Wallet on Multiple Devices?
Yes, a hardware wallet offers multi-device compatibility, enabling users to manage their wallet seamlessly across various platforms. This flexibility enhances wallet management, allowing for secure access and transactions from different devices without compromising security.
How Often Should I Update My Hardware Wallet’s Firmware?
In a digital world reminiscent of a fortress under siege, updating firmware regularly is vital. Experts recommend checking for wallet security updates every few weeks, safeguarding users against vulnerabilities that could jeopardize their precious assets.
Is It Safe to Connect My Hardware Wallet to Public Wi-Fi?
Connecting a hardware wallet to public Wi-Fi poses significant risks. Public Wi-Fi security is often compromised, exposing hardware wallet vulnerabilities that can lead to unauthorized access and potential loss of cryptocurrency. Caution is advised in such situations.
Can I Recover My Wallet if I Forget My PIN?
If someone forgets their PIN, recovery typically isn’t possible due to wallet security measures. However, having a backup phrase can help restore access. It’s vital to securely store recovery phrases separate from the hardware wallet.
Conclusion
To sum up, successfully setting up a cryptocurrency hardware wallet is akin to erecting a fortified bastion to safeguard one’s digital assets against the ever-looming threats of cyber intrusions. With meticulous attention to detail, users can secure their financial future by employing advanced cryptographic protections and user-friendly interfaces. Through ongoing vigilance, including regular updates and secure fund management, individuals solidify their fortress, ensuring their investments remain impervious to the nefarious tactics of digital adversaries in the vast, unpredictable landscape of cryptocurrency.